Do You Have $10M+ to Spare? Why Zero Trust Matters More Than Ever.
$10.22 million.
That’s the average cost of a data breach in the United States in 2025, the highest it’s ever been, according to IBM’s Cost of a Data Breach Report 2025.
Even more worrying is that breaches are getting harder to contain. Shadow AI added $670,000 to the average breach cost. AI-powered phishing attacks now take just minutes to launch. And 97% of AI-related breaches happened on systems that lacked basic access controls.
The trends are clear. Our environments are growing more complex, our attack surfaces are expanding, and our defenses are still built on implicit trust.
That’s the real headline here: the cost of doing nothing is only going up. If you’re not embracing Zero Trust today, you’re budgeting for a breach tomorrow.
A false sense of security is costing us
Globally, average breach costs dropped to $4.44 million, the first decline in five years. According to IBM, the reason is faster response and containment, mostly driven by AI and automation.
But before we celebrate, let’s look closer. U.S. organizations saw costs rise by 9% to $10.22 million. This was driven by increased detection costs and regulatory fines.
Organizations are still operating on trust-based architectures. Too many assume their users, applications, and devices are safe just because they’re inside the perimeter. That assumption is exactly what attackers exploit.
U.S. organizations saw costs rise by 9% to $10.22 million. This was driven by increased detection costs and regulatory fines.
The real breach cost driver: lateral movement
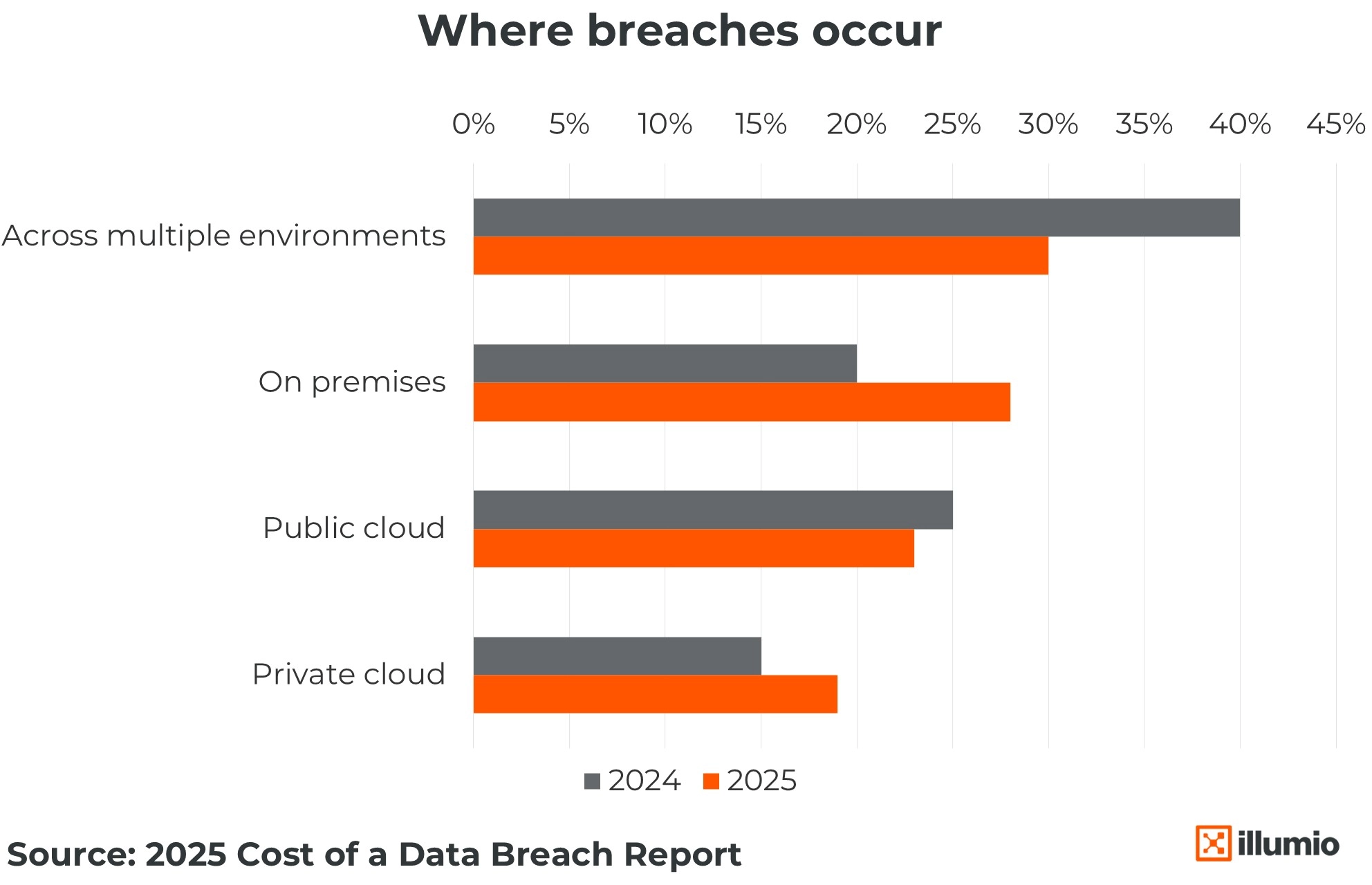
30% of all breaches involved data distributed across multiple environments.
These kinds of breaches take longer to detect, longer to contain, and cost more to recover from.
That’s not a coincidence. When you allow broad, implicit access between environments, you give attackers the freedom to move — undetected — once they’re in. With Zero Trust, that’s the exact risk we’re trying to eliminate.
30% of all breaches involved data distributed across multiple environments.
You don’t stop breaches by building taller walls. You stop them by limiting their blast radius — by isolating workloads, controlling traffic flows, and enforcing least privilege everywhere.
That’s how you stop lateral movement before it causes a $10 million headache.
AI is both a weapon and a widening attack surface
One in six breaches now involve attackers using AI. Think deepfakes, phishing campaigns that take minutes to generate, and highly convincing social engineering at scale.
Even more alarming is that 97% of organizations that experienced AI-related breaches lacked basic access controls. This means they had little to no segmentation, visibility, or data governance. Just open roads for attackers to move laterally.
And then there’s shadow AI — the unmonitored, unsanctioned tools employees spin up without IT’s knowledge. These aren’t just rogue tools, and they’re today’s most exposed attack surfaces.
One in six breaches now involve attackers using AI.
In fact, shadow AI added an average of $670,000 to breach costs. Most of that damage came from compromised customer personally identifiable information (PII), turning a security gap into a massive business risk.
This is where Zero Trust earns its name. It asks the hard, necessary questions:
- What is this workload?
- Should it be communicating with that other workload?
- Can I monitor, restrict, or isolate it — right now?
If the answer is no, your environment is already vulnerable.
Zero Trust isn’t just about securing the systems you know. It’s about uncovering the ones you don’t.
In the age of AI, ignorance is both risky and expensive.
A shrinking window to act
According to the report, only 49% of organizations said they planned to invest more in security after a breach. That’s down from 63% the year before.
This tells me we’re underreacting. The attackers are innovating, scaling, and using AI, while we’re still deciding whether or not to fund our IR plans.
Zero Trust is the only sustainable security strategy in a world where identity is the perimeter, AI is weaponized, and trust is the very thing attackers exploit.
Only 49% of organizations said they planned to invest more in security after a breach. That’s down from 63% the year before.
What the Cost of a Data Breach report should teach us
If you read IBM’s report through a purely statistical lens, you’ll walk away informed.
But if you read it through the lens of Zero Trust, I believe you’ll walk away more motivated than ever.
This report is a warning sign. It tells us that attack surfaces are expanding, breach costs are rising where governance is weak, and the status quo isn’t working.
It also shows us what does work: faster containment, tighter controls, and AI used to defend instead of destroy.
The organizations that treat Zero Trust as a strategy, not a here-and-gone buzzword, are the ones that will stay resilient, secure, and ready for whatever comes next.