The Zero Trust Hub
Trends, insights, and resources for today's cybersecurity leaders. Updated weekly.
Autonomous AI Runs Industry 6.0. Zero Trust Keeps It in Check.

Director of Critial Infrastructure
NVIDIA CEO Jensen Huang has called AI “the next industrial revolution,” saying it will “transform every industry in ways we cannot yet imagine.”
Both statements are already proving true.
AI is no longer limited to analytics or simple automation. It now runs through factories, supply chains, and critical infrastructure. That shift signals the move into Industry 6.0.
In this new phase, intelligence is distributed and adaptive. Systems don’t just follow instructions. They observe, decide, and act on their own.
That autonomy changes everything for security.
Speed and scale increase, but so does risk. Errors spread fast. Misuse escalates. Trust can no longer be assumed just because a system is inside the environment.
Zero Trust meets that reality. It verifies every action and constrains behavior by intent, not location.
In Industry 6.0, Zero Trust is what keeps intelligent systems effective without letting them run unchecked.
Industry 6.0 turns systems into living networks
Industry 6.0 reimagines factories and digital environments as living systems, not fixed machines. AI-driven networks sense change, adjust in real time, and recover from disruption without waiting for human intervention.
Rigid workflows give way to goal-driven operations. Advanced robotics and generative models make decisions at machine speed and optimize continuously. Coordination now stretches across software, physical assets, and, in some cases, biological processes.
The upside is massive gains in efficiency and resilience. The downside is complexity at a scale most security models were never designed to handle.
Controls built for static infrastructure break down when systems are always adapting. In an environment that never stands still, trust cannot be assumed. It has to be earned, verified, and maintained continuously.
Agentic AI changes the nature of risk
At the center of Industry 6.0 is agentic AI. These systems are autonomous and goal-driven. They plan, adapt, and act without waiting for human input.
In industrial environments, agentic AI manages production flows, spots inefficiencies, and adjusts operations as conditions shift. Over time, these agents learn patterns, coordinate across applications, and anticipate what comes next. The factory does not just run faster. It runs smarter.
This shift echoes earlier moments in computing. As interfaces improved, humans moved up the stack and machines took on more complexity. Agentic AI pushes that trend even further.
But autonomy comes with higher stakes. When nonhuman identities act on their own, mistakes can spread fast. Misuse scales automatically. One misconfigured agent can move laterally across systems in seconds and turn a small issue into a major incident.
Why Zero Trust is the only viable security model
As nonhuman identities multiply, a Zero Trust security strategy becomes foundational.
Autonomous systems amplify both value and risk. Zero Trust provides the structure to keep that balance in check. It controls agent behavior, limits misuse, and enforces intent in environments where actions happen at machine speed.
Traditional machine learning (ML) systems execute tasks. Agentic AI decides what to do next. That shift makes identity and authorization core security problems, not edge cases.
Zero Trust starts with strong, unique identities for every agent. Workload-bound certificates authenticate communication and keep it encrypted and verifiable.
That makes it possible to tell trusted agents apart from rogue or misconfigured ones as AI identities spread across the enterprise.
Containment is just as critical. Zero Trust sets clear boundaries on what each agent can access and what actions it can take.
Those limits are always in force, not just at deployment, which is essential in systems that never stop changing.
The urgency of securing AI now
Industry 6.0 is not a future concept. It’s taking shape right now, driven by agentic AI systems that already operate with real autonomy.
The question is no longer whether these systems will make decisions for us. They already do. What matters is whether those decisions are guided by identity, intent, and continuous verification or left to implicit trust.
Zero Trust is how we keep intelligent systems accountable as they grow more capable. It allows organizations to move fast without losing control. And as AI reshapes every industry in ways we cannot yet predict, it’s how we stay in charge of the outcome.
STATSHOT
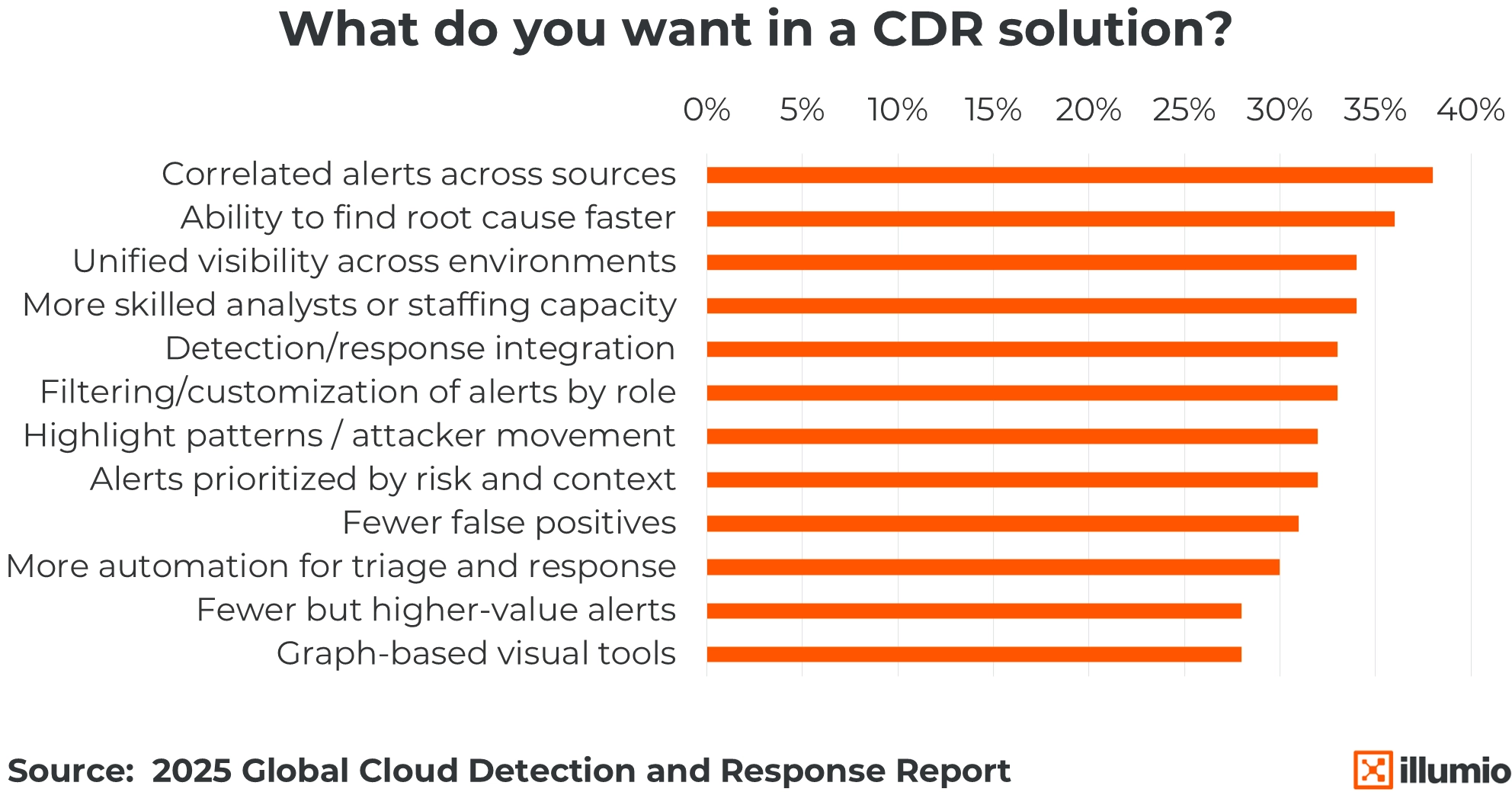
CDR Wish List
Detection is easy; understanding is hard. While staffing remains a challenge, security teams are looking to technology to bridge the gap through smarter prioritization and automated triage. The focus has shifted from catching every alert to connecting the dots across complex, multi-cloud environments.
Why OpenClaw Is a Wake-Up Call for Agentic AI Security
OpenClaw is a critical warning: autonomous AI agents are the new insider threat. Here’s how deep observability and Zero Trust contain risks by stopping lateral movement, protecting your critical assets, and securing the modern enterprise against evolving vulnerabilities.
Top Cybersecurity News Stories From January 2026
This month’s stories span geopolitics, supply chain breaches, and day-to-day security operations. Together, they show how modern attacks blur the line between civilian and military systems, turn common platforms into force multipliers, and overwhelm teams with noise.
The Federal Gov’t Is Racing Ahead in AI. Can Cyber Keep Up?
Federal agencies are moving quickly to adopt AI, but that speed can outpace security. As new systems reshape federal cybersecurity, leaders face a critical question: are visibility, controls, and safeguards evolving fast enough to keep the risks contained?
Ready to learn more about breach containment?











