No More Chewy Centers: Reflecting on 15 Years of Zero Trust Cybersecurity
In 2008, I was working as an analyst at Forrester Research, spending my days knee-deep in reports, client calls, and frustrating conversations with security leaders trying to protect networks that weren’t designed for modern threats.

Trust itself was the issue. The fact that we had injected trust, a human emotion, into digital systems was the issue. We were trusting users, devices, networks, and that trust was being exploited again and again.
We described networks as hard on the outside but soft and chewy on the inside.
I realized that if we kept trusting what’s inside the network, we’re only giving attackers a free pass once they get past the perimeter.
All packets and systems should have the same trust level: zero. That’s why I called it Zero Trust.
It’s a strategy designed to stop data breaches and contain adversaries by eliminating trust and strictly enforcing access.
Yesterday, Zero Trust officially turned 15 years old. I wanted to take the opportunity to reflect on the strategy’s nearly two decades in the cybersecurity industry.
Zero Trust: the world’s only true cyber strategy
From day one, Zero Trust was a strategy. And to this day, it remains the world’s only true cybersecurity strategy. It’s a framework that aligns your defenses with the realities of how attackers operate.
If you’re connected to the internet, you’re already proximate to attackers. They always have the potential to strike and likely have the will. This means a cyberattack is always imminent.
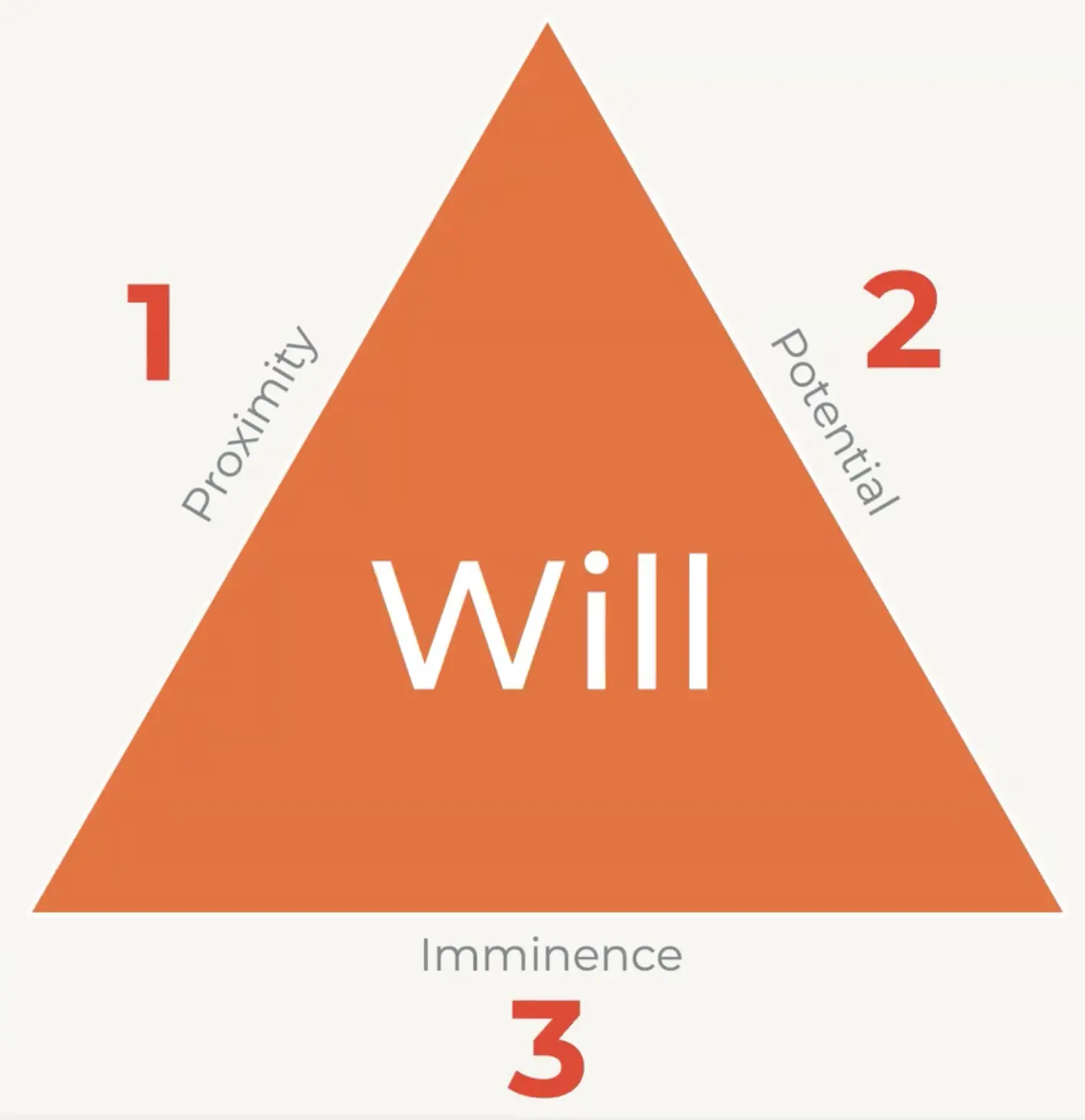
You can’t stop attackers from trying, but you can keep them from succeeding.
That’s the power of Zero Trust. It eliminates unnecessary allow rules that let attackers move through your network and exfiltrate your data.
Breaches can succeed only when policy allows them to. With Zero Trust, you can prevent intrusions from escalating into crises.
From a research paper to a presidential mandate
When I published my original Zero Trust research at Forrester in 2010, I never imagined it would reach this scale. It certainly didn’t catch fire early on. Its success was a slow uptick.
In the last 15 years, the world has caught up to the need for real cybersecurity strategy. Zero Trust is now a foundational principle at every level.
The U.S. federal government made that official in 2021 with Executive Order 14028. For the first time, Zero Trust wasn’t just a recommendation but a mandate. Agencies were told to stop trusting internal networks, adopt modern defenses, and treat Zero Trust as a journey — not a checkbox.
That Executive Order was a milestone. It validated what many of us in the industry have been saying for years: perimeter-based security is obsolete, and segmentation-driven Zero Trust is the way forward.
Segmentation is the foundation of Zero Trust
Over the years, many have wanted to make Zero Trust about identity. Identity is important — don’t get me wrong. But it’s segmentation, not identity, that’s at the core of Zero Trust.
I’ve been talking about segmentation for years. The second report ever written on Zero Trust was one I also wrote in 2010, Build Security Into Your Network’s DNA: The Zero Trust Network Architecture.

In the report, I recognized the importance of segmentation and centralized management as key components of Zero Trust and wrote: “New ways of segmenting networks must be created because all future networks need to be segmented by default.”
You can't enforce a policy unless you can isolate systems. Segmentation is what lets us apply the Kipling Method: allow users to access only specific resources for specific reasons, in specific contexts. It’s the “who, what, when, where, why, and how” of Zero Trust rule writing.
If you're not segmenting your environment, you're not doing Zero Trust. It’s that simple.
Why AI doesn’t change Zero Trust
Everywhere you turn, people are talking about AI. It’s exciting, it’s powerful, and it’s very dangerous if not controlled.
But AI doesn’t change the fundamentals of Zero Trust. It reinforces them. In fact, Zero Trust is the strategy that allows you to safely embrace AI.
Without strict segmentation, policy enforcement, and control over data flows, AI becomes another soft and chewy center waiting to be exploited.
Zero Trust helps you define what AI systems can access, how they behave, and how to contain them if something goes wrong. You don’t need a new security strategy for AI. You just need to apply the right one. That’s Zero Trust.
Ready for whatever comes next
Zero Trust isn’t just built for the past 15 years. It’s ready for the next 15 and beyond.
Zero Trust is anti-fragile. It gets stronger under pressure, and that’s why it’s still here after all this time.
Whether it’s AI, quantum, or threats we haven’t even imagined yet, Zero Trust gives us a strategy that adapts, endures, and wins.


