The Zero Trust Hub Editions
Zero Trust Segmentation trends, insights, and resources for today's cybersecurity leaders
Zero Trust Doesn’t Fail Because of Tech. It Fails Because of Leadership.

Vice President, Industry Strategy
On Tony Scott’s first day as U.S. Federal Chief Information Officer (CIO), he found himself sitting in the Oval Office with President Obama and Vice President Biden.
He didn’t get the luxury of easing into the role. Just immediate responsibility at the highest possible level.
Tony admitted what many leaders feel but rarely say out loud: “What am I doing here?” It was a flash of imposter syndrome and the realization that if something goes wrong, it was on him.
That moment matters because it explains Tony Scott’s approach to Zero Trust.
After decades as CIO at Microsoft, VMware, Disney, and ultimately the U.S. federal government, Tony has seen one truth repeat itself over and over again. Security doesn’t break because leaders don’t know what to do but because they don’t operationalize it.
And nowhere is that more obvious than in how organizations approach Zero Trust.
Zero Trust is an execution problem, not a strategy problem
When Tony reflects on the most consequential cybersecurity moment of his career, he points to the 2015 Office of Personnel Management (OPM) breach.
The breach was a classic identity-based attack. Bad actors got their hands on compromised credentials with too much access privilege.
This allowed them to break into systems that weren’t patched and steal the personal data of over 21 million individuals, including federal employees and contractors.
Multi-factor authentication (MFA) could’ve prevented, or at least slowed down, attackers. The OPM had purchased MFA technology, but no one had ever operationalized it.
Federal guidance requiring MFA had been issued ten years earlier. Adoption sat at roughly 50% across all agencies.
Elevated privileges were rampant, and critical vulnerabilities piled up because “there were other priorities.”
It highlights an uncomfortable reality in cybersecurity across both public and private sectors. Most security failures happen in the gap between intent and enforcement. And filling that gap comes down to leadership’s initiative to get it done.
The OPM lesson: accountability means everything
After the breach, Tony and his team decided the best solution was to get MFA implemented — for real this time.
They created a scorecard to hold agencies accountable during the process. And every week, the President saw the numbers, encouraging agencies to prioritize implementation.
The results were immediate.
Within weeks:
- MFA adoption across agencies jumped into the mid-90% range
- Elevated privileges dropped by roughly two-thirds
- Hundreds of thousands of critical vulnerabilities were reduced to a few hundred
Nothing about the technology changed overnight. Instead, it was leadership that made expectations explicit, progress visible, and failure uncomfortable.
Zero Trust only works when someone owns the outcome
This is where Tony’s perspective cuts through a lot of Zero Trust noise.
Many organizations spend endless time debating where the CISO should report, which tools “count” as Zero Trust, and whether Zero Trust is realistic.
Tony dismisses most of that as distraction. What actually matters is whether security leaders have:
- Full visibility into cyber risk
- Authority to act on that risk
- Direct access to executive and board-level decision makers
Tony compares the CISO role to the head of audit. It may sit inside the organization, but it ultimately works for the board.
If security leaders can’t escalate, enforce, and measure outcomes, Tony believes that a Zero Trust strategy can collapse into security theater.
Zero Trust fails without leadership commitment to execution
According to Tony, Zero Trust doesn’t fail because teams lack the right tech but because leaders accept partial execution. In the real world, partial execution is indistinguishable from failure.
And in an era of escalating attacks, regulatory scrutiny, and nonstop disruption, intent without enforcement is a liability.
Tony’s career proves that when leaders make security measurable, visible, and unavoidable, genuine change can happen fast.
The organizations that get this right will be the ones still standing when everyone else is explaining what went wrong.
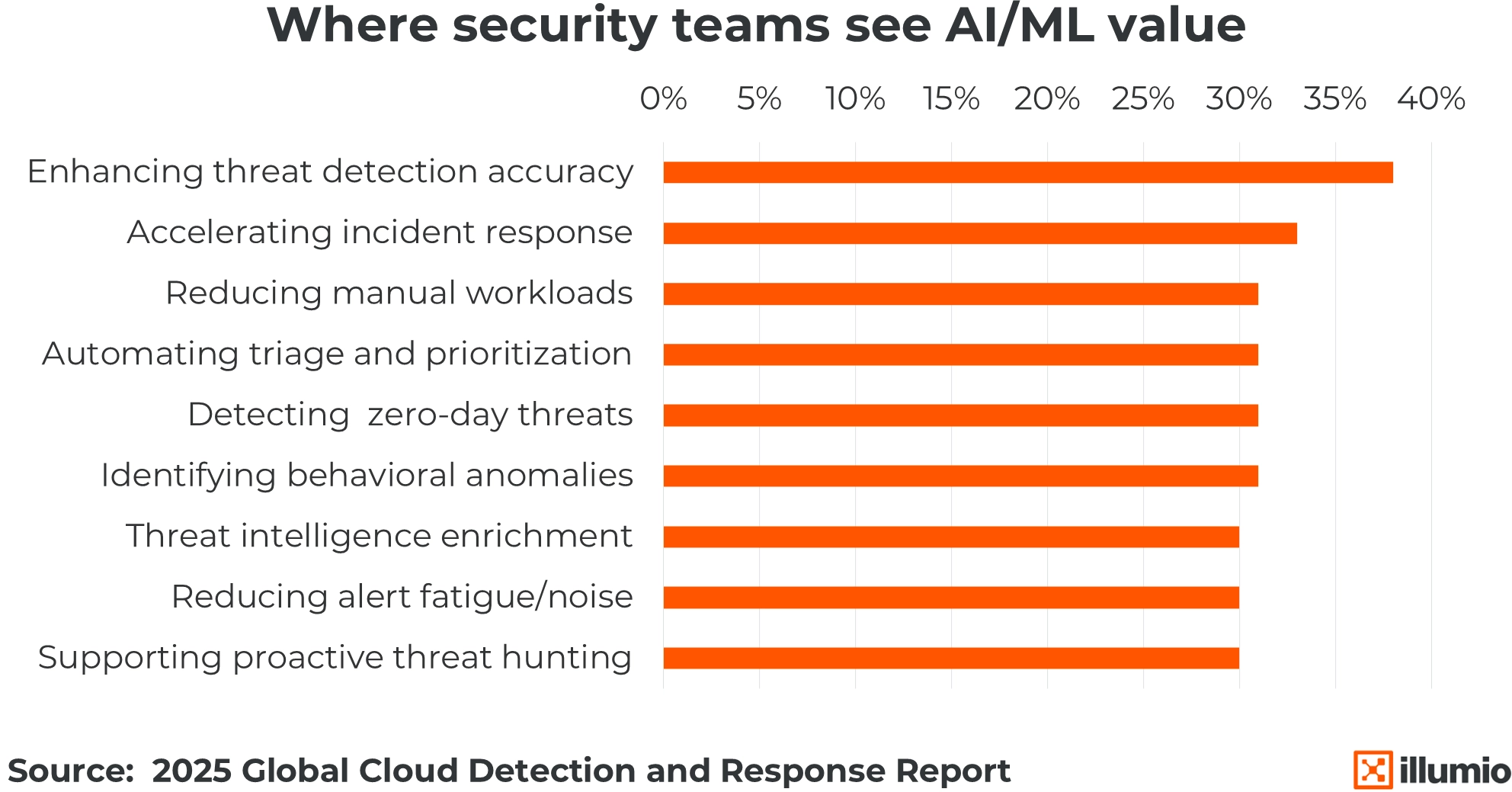
STATSHOT
What AI Delivers
AI and machine learning are no longer buzzwords — they’re delivering results. The top value? Precision. It's also boosting incident response times, cutting down manual tasks, and surfacing critical threats faster. From automating triage to flagging zero-days and behavioral anomalies, AI and machine learning are reshaping SecOps. It’s proof that AI in cybersecurity is more than hype; it’s a force multiplier.